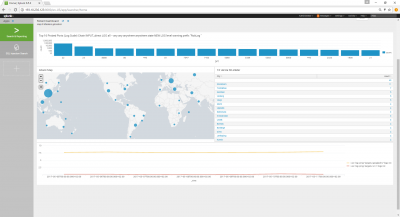
Visualization of FirewallD-logs in SPLUNK
From Datateknik
(Difference between revisions)
(Created page with "hej = FirewallD logs in SPLUNK = Check that you have a text-file (log) with ip attack data (use less ...) ==Install SPLUNK== *install splunk <font color=red>do NOT install sp...") |
|||
| Line 1: | Line 1: | ||
hej | hej | ||
| + | [[File:splunk-screenshot1.png|left|400px|caption]] | ||
= FirewallD logs in SPLUNK = | = FirewallD logs in SPLUNK = | ||
Check that you have a text-file (log) with ip attack data (use less ...) | Check that you have a text-file (log) with ip attack data (use less ...) | ||
Revision as of 08:46, 11 May 2017
hej
Contents |
FirewallD logs in SPLUNK
Check that you have a text-file (log) with ip attack data (use less ...)
Install SPLUNK
- install splunk do NOT install splunk if you alreade have installed it
wget -O splunk-6.5.3-36937ad027d4-linux-2.6-x86_64.rpm 'https://www.splunk.com/bin/splunk/DownloadActivityServlet?architecture=x86_64&platform=linux&version=6.5.3&product=splunk&filename=splunk-6.5.3-36937ad027d4-linux-2.6-x86_64.rpm&wget=true' echo "--------------------------" yum localinstall splunk-6.5.3-36937ad027d4-linux-2.6-x86_64.rpm rpm -ql splunk | grep splunk$ echo "--------------------------" # firewall-cmd --add-rich-rule='rule family="ipv4" port port="8000" protocol="tcp|udp" accept'
Import data into splunk
Not so difficult